secure network design
From a practical standpoint it is rapidly becoming a requirement to design for reliable secure remote access. Ad Test your users identify their weaknesses and create a custom security training program.
Network Security Network Design Services
Ad Let us help you maintain a secured computing infrastructure with top level IT security.
. A network added between a protected network and an external network in order to provide an additional layer of security A DMZ is sometimes called a Perimeter network or a Three. Hackers once on to a network often go undetected as they freely move from system to system looking for valuable. The BCF design model is referenced to implement security networkwide with no reliance to a single technology.
This is the point at which users and devicesincluding mobile and. Ad No Matter Your Mission Get The Right Security Systems To Accomplish It. Converting decimal numbers to binary and hexadecimal numberspptx.
Creation physical protection network design monitoring access and control data flow analysis secure feature sets from common network components and user interaction with the system. Ad 100 cloud based Radius SaaS for certificate based authentication for WIFI LAN and VPN. Chapter 12 VPN Technologiespdf.
Perfect match for the super-easy SCEPman cloud PKI. Save Time Money - Start Now. Networks are complex systems of many components that operate in an insecure world.
Educate your staff to recognize the next phishing attack. Endpoint security controls such as endpoint detection and response and cloud access security brokers. In this course you will learn how to.
Is your computer and network secured. Anagnostopoulos Shuai Chen University of Passau. The Ultra-Secure Network Architecture.
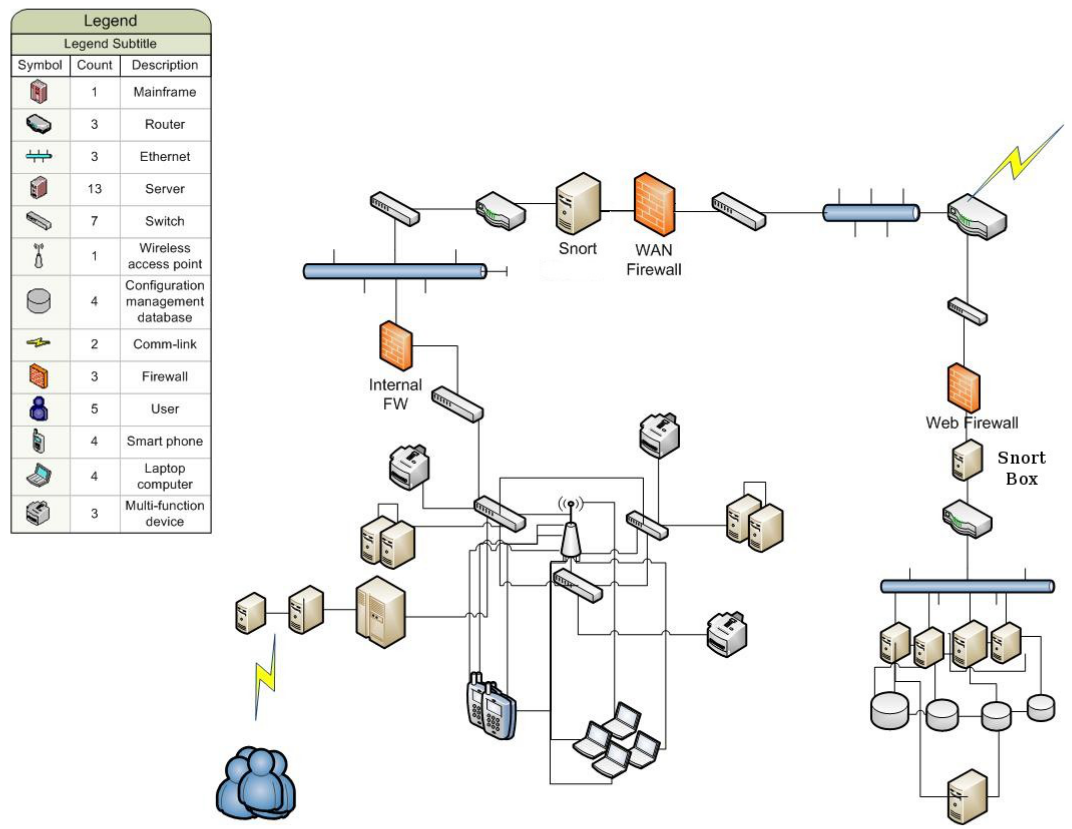
Figure 1 Secure Network Foundation Design for Single Site Deployments Solution Components The main office router platform was selected for this design based on the number of. Secure Network Design C700. Ad Detect threats identify vulnerabilities and harden configurations in real time.
COMPUTER S C700 - Spring 2018. ARTICLE Basic Internet Network Architecture Practices. A Design for a Secure Network of Networks Using a Hardware and Software Co-Engineering Architecture Nico Mexis Nikolaos A.
The typical architectural diagram shown below offers only two slim layers. Some network security design best practices include paying particular attention to the edge of your network. Network security layering can involve the following.
Call now to schedule your demo. Up to 50 cash back Secure Network Design. Cybersecurity products for enterprise industrial organizations.
With todays converged networks proper. Secure Network Design. PKIs with OCSP supported.
Do you have proper firewalls and security in place. Review the Best Network Security Systems for 2022. Edge Subscriber Policy Security.

5 Top Network Design Considerations For Security Integrators 2019 01 28 Sdm Magazine
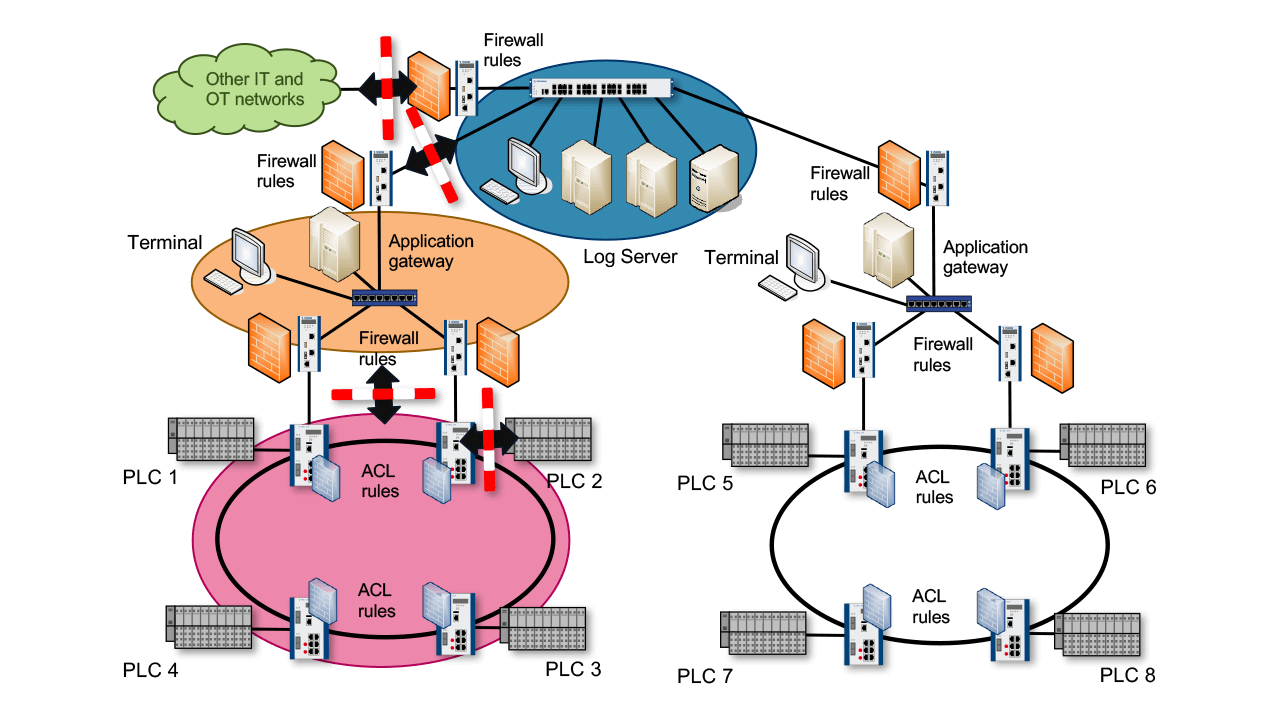
Designing Industrial Networks From A Security Point Of View Industrial Ethernet Book

Security Architecture Secure Network Design Iins 210 260
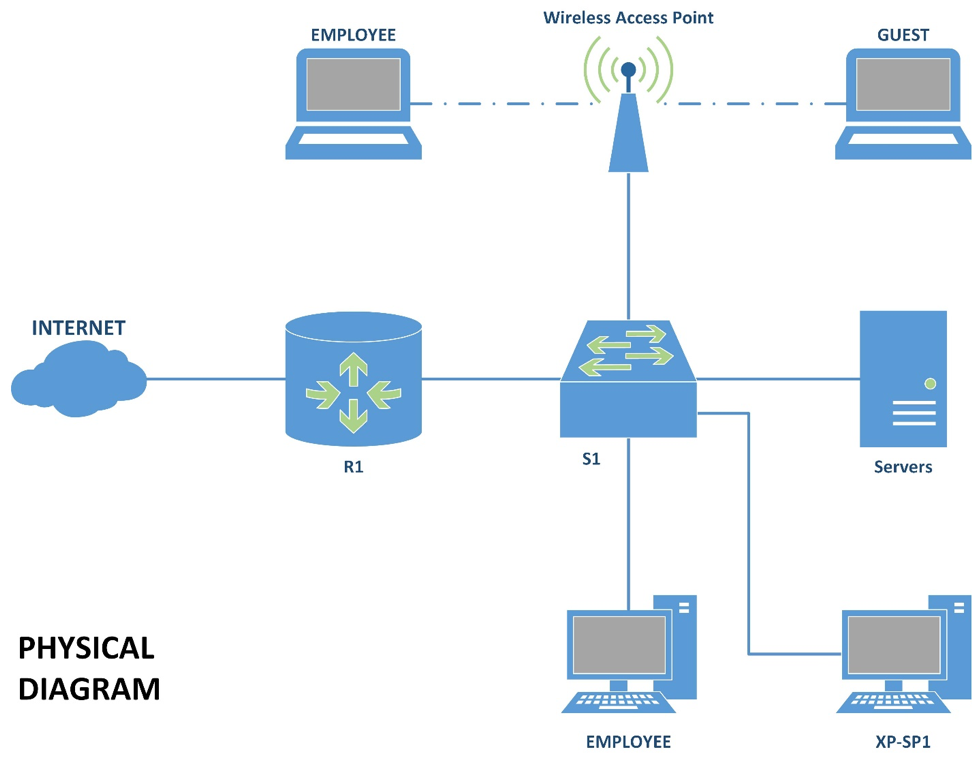
Secure By Design The Network At T Cybersecurity

Secure Network Design In Visio By Tech Jayesh Fiverr

The Ultra Secure Network Architecture

Figure 1 From Design And Implementation Of A Network Security Model For Cooperative Network Semantic Scholar
0 Response to "secure network design"
Post a Comment